typedef struct {
ULONG i[2]; /* number of _bits_ handled mod 2^64 */
ULONG buf[4]; /* scratch buffer */
unsigned char in[64]; /* input buffer */
unsigned char digest[16]; /* actual digest after MD5Final call */
} MD5_CTX;
#define MD5DIGESTLEN 16
typedef void(WINAPI* PMD5Init)(MD5_CTX *);
typedef void(WINAPI* PMD5Update)(MD5_CTX *, const unsigned char *,
unsigned int);
typedef void(WINAPI* PMD5Final)(MD5_CTX *);
BOOL CalcMd5(unsigned char * data, unsigned int len, char *digest)
{
MD5_CTX ctx;
HMODULE hDLL;
BOOL ret = FALSE;
SecureZeroMemory(digest, MD5DIGESTLEN);
hDLL = LoadLibraryA("advapi32.dll");
if (hDLL) {
PMD5Init MD5Init = (PMD5Init)GetProcAddress(hDLL, "MD5Init");
PMD5Update MD5Update = (PMD5Update)GetProcAddress(hDLL, "MD5Update");
PMD5Final MD5Final = (PMD5Final)GetProcAddress(hDLL, "MD5Final");
if (MD5Init && MD5Update && MD5Final) {
MD5Init(&ctx);
MD5Update(&ctx, data, len);
MD5Final(&ctx);
memcpy(digest, ctx.digest, MD5DIGESTLEN);
ret = TRUE;
}
FreeLibrary(hDLL);
}
return ret;
}
-
Windows API 计算MD5
-
PGP License
Command Line
DAAY2-UUE69-LE950-RAZ0L-2AW5N-ANA
Desktop
D4R6W-PQBCD-FFF6L-K950U-Q5XRV-DYC
-
C#格式化卷
using System.Management; public bool FormatVolume(string VolumeHeader, string label) { if (VolumeHeader.Length != 2 || VolumeHeader[1] != ':' || !char.IsLetter(VolumeHeader[0])) return false; bool result = false; ManagementObjectSearcher searcher = new ManagementObjectSearcher(@"select * from Win32_Volume WHERE DriveLetter = '" + VolumeHeader + "'"); foreach (ManagementObject mo in searcher.Get()) { object so = mo.InvokeMethod("Format", new object[] { "NTFS", true, 4096, label, false }); if ("0" == so.ToString()) { result = true; } } return result; }
-
将当前用户设定为某注册表键的所有者,并使其拥有完全访问权限
#include <Windows.h> #include <Aclapi.h> bool AdjustPrivileges(char* SeName) { HANDLE hToken = NULL; TOKEN_PRIVILEGES tp; TOKEN_PRIVILEGES oldtp; DWORD dwSize = sizeof(TOKEN_PRIVILEGES); LUID luid; SecureZeroMemory(&tp, sizeof(tp)); SecureZeroMemory(&oldtp, sizeof(oldtp)); SecureZeroMemory(&luid, sizeof(luid)); if (OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, &hToken) == FALSE) { if (GetLastError() == ERROR_CALL_NOT_IMPLEMENTED) return true; else return false; } if (LookupPrivilegeValueA(NULL, SeName, &luid) == FALSE) { CloseHandle(hToken); return false; } tp.PrivilegeCount = 1; tp.Privileges[0].Luid = luid; tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED; bool r = AdjustTokenPrivileges(hToken, FALSE, &tp, sizeof(TOKEN_PRIVILEGES), &oldtp, &dwSize) ? true : false; CloseHandle(hToken); return r; }; bool TakeOwnerAndSetCurrentUserFullAccess(HKEY hKey) { CHAR UserName[36]; DWORD cbUserName = sizeof(UserName); CHAR Sid[1024]; DWORD cbSid = sizeof(Sid); CHAR DomainBuffer[128]; DWORD cbDomainBuffer = sizeof(DomainBuffer); SID_NAME_USE eUse; PACL Dacl = NULL, OldDacl = NULL; EXPLICIT_ACCESS Ea; PSECURITY_DESCRIPTOR Sd = NULL; bool r = false; SecureZeroMemory(Sid, sizeof(Sid)); SecureZeroMemory(DomainBuffer, sizeof(DomainBuffer)); if (AdjustPrivileges(SE_TAKE_OWNERSHIP_NAME) && AdjustPrivileges(SE_RESTORE_NAME)) { GetUserNameA(UserName, &cbUserName); if (LookupAccountNameA(NULL, UserName, &Sid, &cbSid, DomainBuffer, &cbDomainBuffer, &eUse)) { SecureZeroMemory(&Ea, sizeof(EXPLICIT_ACCESS)); GetSecurityInfo(hKey, SE_REGISTRY_KEY, DACL_SECURITY_INFORMATION, NULL, NULL, &OldDacl, NULL, &Sd); BuildExplicitAccessWithNameA(&Ea, UserName, GENERIC_ALL, GRANT_ACCESS, SUB_CONTAINERS_AND_OBJECTS_INHERIT); if (SetEntriesInAclA(1, &Ea, OldDacl, &Dacl) == ERROR_SUCCESS) { //更改所有者 DWORD result = SetSecurityInfo(hKey, SE_REGISTRY_KEY, OWNER_SECURITY_INFORMATION, &Sid, NULL, NULL, NULL); if (result != ERROR_SUCCESS) { DWORD errCode = GetLastError(); } //添加完全控制权限,如果所有者没添加成功,但是当前用户有操作该文件的权限,那么依旧可以添加完全控制权限 if (SetSecurityInfo(hKey, SE_REGISTRY_KEY, DACL_SECURITY_INFORMATION, &Sid, NULL, Dacl, NULL) == ERROR_SUCCESS) { r = true; } } } } return r; }
-
获取Windows操作系统真实版本
无视Windows兼容模式获取Windows操作系统真实版本。
bool GetWindowsVersion(DWORD *wMajorVersion, DWORD *wMinorVersion, DWORD *wServicePackMajor) { RTL_OSVERSIONINFOEXW verInfo; RtlSecureZeroMemory(&verInfo, sizeof(verInfo)); verInfo.dwOSVersionInfoSize = sizeof(verInfo); typedef NTSTATUS(NTAPI* fnRtlGetVersion)(PRTL_OSVERSIONINFOW lpVersionInformation); fnRtlGetVersion RtlGetVersion = (fnRtlGetVersion)GetProcAddress(GetModuleHandleA("ntdll.dll"), "RtlGetVersion"); if (RtlGetVersion != 0 && RtlGetVersion((PRTL_OSVERSIONINFOW)&verInfo) == 0) { if (wMajorVersion) *wMajorVersion = verInfo.dwMajorVersion; if (wMinorVersion) *wMinorVersion = verInfo.dwMinorVersion; if (wServicePackMajor) *wServicePackMajor = verInfo.wServicePackMajor; return true; } return false; }
-
boost_asio_ssl demo
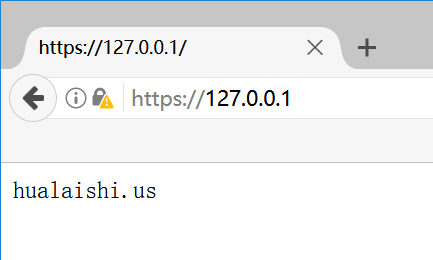
#include <cstdlib> #include <iostream> #include <boost/bind.hpp> #include <boost/asio.hpp> #include <boost/asio/ssl.hpp> #pragma comment(lib,"libcrypto.lib") #pragma comment(lib,"libssl.lib") #pragma comment(lib,"crypt32") using ssl_socket = boost::asio::ssl::stream<boost::asio::ip::tcp::socket>; class session { public: session(boost::asio::io_service& io_service, boost::asio::ssl::context& context) : socket_(io_service, context) { page_ = "HTTP/1.1 200 OK\r\nServer: squid / 3.5.20\r\nContent - Type: text / html; charset = GB2312\r\nContent-Length: 12\r\n\r\nhualaishi.us"; } ssl_socket::lowest_layer_type& socket() { return socket_.lowest_layer(); } void start() { socket_.async_handshake(boost::asio::ssl::stream_base::server, boost::bind(&session::handle_handshake, this, boost::asio::placeholders::error)); } void handle_handshake(const boost::system::error_code& error) { if (!error) { socket_.async_read_some(boost::asio::buffer(data_, max_length), boost::bind(&session::handle_read, this, boost::asio::placeholders::error, boost::asio::placeholders::bytes_transferred)); } else { delete this; } } void handle_read(const boost::system::error_code& error, size_t bytes_transferred) { if (!error) { boost::asio::async_write(socket_, boost::asio::buffer(page_), boost::bind(&session::handle_write, this, boost::asio::placeholders::error)); } else { delete this; } } void handle_write(const boost::system::error_code& error) { if (!error) { socket_.async_read_some(boost::asio::buffer(data_, max_length), boost::bind(&session::handle_read, this, boost::asio::placeholders::error, boost::asio::placeholders::bytes_transferred)); } else { delete this; } } private: ssl_socket socket_; enum { max_length = 1024 }; char data_[max_length]; std::string page_; }; class server { public: server(boost::asio::io_service& io_service, unsigned short port) : io_service_(io_service), acceptor_(io_service, boost::asio::ip::tcp::endpoint(boost::asio::ip::tcp::v4(), port)), context_(io_service, boost::asio::ssl::context::sslv23) { context_.set_options( boost::asio::ssl::context::default_workarounds | boost::asio::ssl::context::no_sslv2 | boost::asio::ssl::context::single_dh_use); context_.set_password_callback(boost::bind(&server::get_password, this)); context_.use_certificate_chain_file("server.cer"); context_.use_private_key_file("server.pem", boost::asio::ssl::context::pem); context_.use_tmp_dh_file("dh512.pem"); session* new_session = new session(io_service_, context_); acceptor_.async_accept(new_session->socket(), boost::bind(&server::handle_accept, this, new_session, boost::asio::placeholders::error)); } std::string get_password() const { return "123456"; } void handle_accept(session* new_session, const boost::system::error_code& error) { if (!error) { new_session->start(); new_session = new session(io_service_, context_); acceptor_.async_accept(new_session->socket(), boost::bind(&server::handle_accept, this, new_session, boost::asio::placeholders::error)); } else { delete new_session; } } private: boost::asio::io_service& io_service_; boost::asio::ip::tcp::acceptor acceptor_; boost::asio::ssl::context context_; }; int main(int argc, char* argv[]) { try { if (argc != 2) { std::cerr << "Usage: server <port>\n"; return 1; } boost::asio::io_service io_service; //using namespace std; // For atoi. server s(io_service, std::atoi(argv[1])); io_service.run(); } catch (std::exception& e) { std::cerr << "Exception: " << e.what() << "\n"; } return 0; }#include <cstdlib> #include <iostream> #include <boost/bind.hpp> #include <boost/asio.hpp> #include <boost/asio/ssl.hpp> #pragma comment(lib,"libcrypto.lib") #pragma comment(lib,"libssl.lib") #pragma comment(lib,"crypt32") enum { max_length = 1024 }; class client { public: client(boost::asio::io_service& io_service, boost::asio::ssl::context& context, boost::asio::ip::tcp::resolver::iterator endpoint_iterator) : socket_(io_service, context) { socket_.set_verify_mode(boost::asio::ssl::verify_peer); socket_.set_verify_callback( boost::bind(&client::verify_certificate, this, _1, _2)); boost::asio::async_connect(socket_.lowest_layer(), endpoint_iterator, boost::bind(&client::handle_connect, this, boost::asio::placeholders::error)); } bool verify_certificate(bool preverified, boost::asio::ssl::verify_context& ctx) { // The verify callback can be used to check whether the certificate that is // being presented is valid for the peer. For example, RFC 2818 describes // the steps involved in doing this for HTTPS. Consult the OpenSSL // documentation for more details. Note that the callback is called once // for each certificate in the certificate chain, starting from the root // certificate authority. // In this example we will simply print the certificate's subject name. char subject_name[256]; X509* cert = X509_STORE_CTX_get_current_cert(ctx.native_handle()); X509_NAME_oneline(X509_get_subject_name(cert), subject_name, 256); std::cout << "Verifying " << subject_name << "\n"; return preverified; } void handle_connect(const boost::system::error_code& error) { if (!error) { socket_.async_handshake(boost::asio::ssl::stream_base::client, boost::bind(&client::handle_handshake, this, boost::asio::placeholders::error)); } else { std::cout << "Connect failed: " << error.message() << "\n"; } } void handle_handshake(const boost::system::error_code& error) { if (!error) { std::cout << "Enter message: "; std::cin.getline(request_, max_length); size_t request_length = strlen(request_); boost::asio::async_write(socket_, boost::asio::buffer(request_, request_length), boost::bind(&client::handle_write, this, boost::asio::placeholders::error, boost::asio::placeholders::bytes_transferred)); } else { std::cout << "Handshake failed: " << error.message() << "\n"; } } void handle_write(const boost::system::error_code& error, size_t bytes_transferred) { if (!error) { boost::asio::async_read(socket_, boost::asio::buffer(reply_, bytes_transferred), boost::bind(&client::handle_read, this, boost::asio::placeholders::error, boost::asio::placeholders::bytes_transferred)); } else { std::cout << "Write failed: " << error.message() << "\n"; } } void handle_read(const boost::system::error_code& error, size_t bytes_transferred) { if (!error) { std::cout << "Reply: "; std::cout.write(reply_, bytes_transferred); std::cout << "\n"; } else { std::cout << "Read failed: " << error.message() << "\n"; } } private: boost::asio::ssl::stream<boost::asio::ip::tcp::socket> socket_; char request_[max_length]; char reply_[max_length]; }; int main(int argc, char* argv[]) { try { if (argc != 3) { std::cerr << "Usage: client <host> <port>\n"; return 1; } boost::asio::io_service io_service; boost::asio::ip::tcp::resolver resolver(io_service); boost::asio::ip::tcp::resolver::query query(argv[1], argv[2]); boost::asio::ip::tcp::resolver::iterator iterator = resolver.resolve(query); boost::asio::ssl::context ctx(boost::asio::ssl::context::sslv23); ctx.load_verify_file("ca.pem"); client c(io_service, ctx, iterator); io_service.run(); } catch (std::exception& e) { std::cerr << "Exception: " << e.what() << "\n"; } return 0; }
-
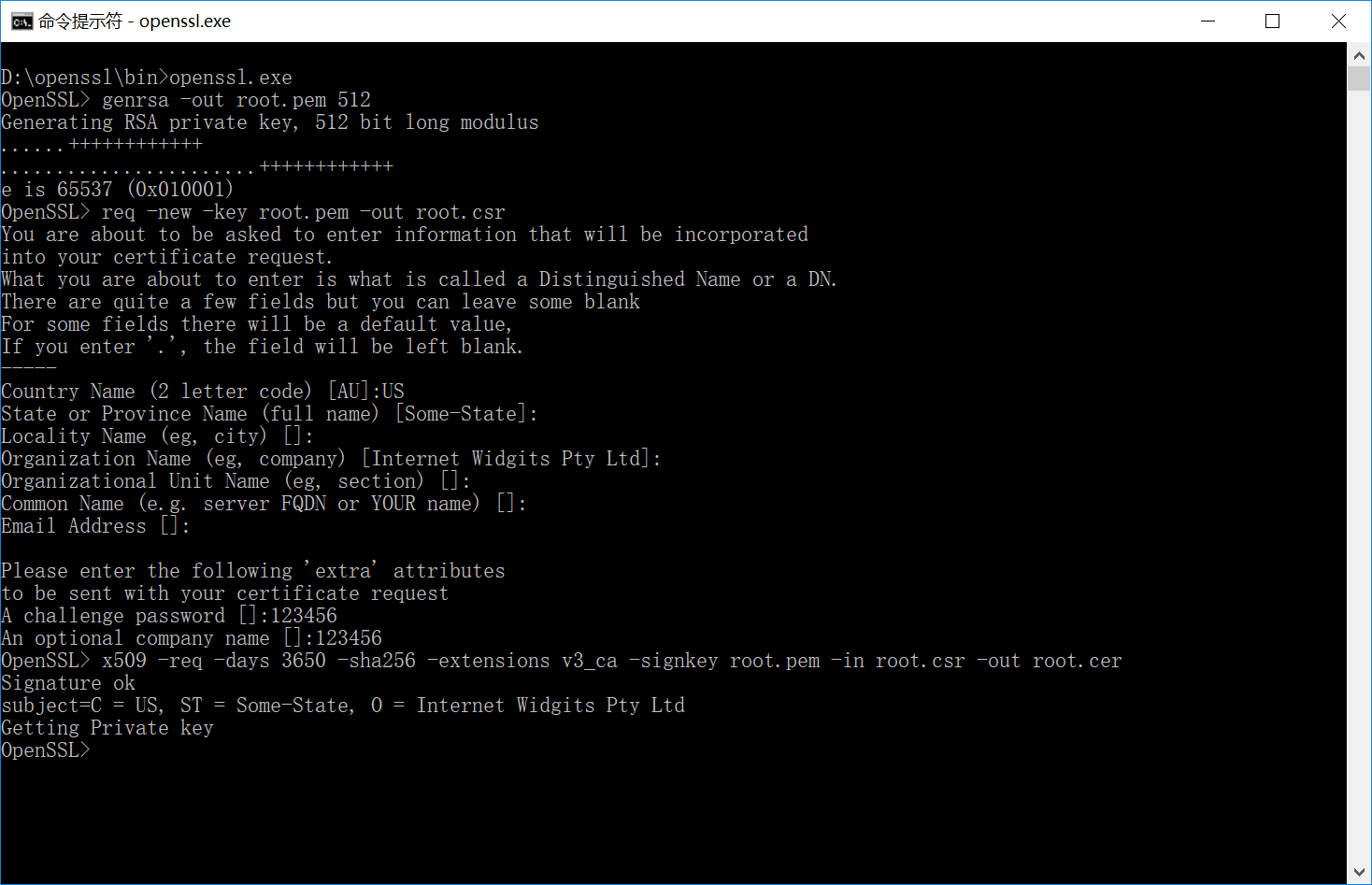
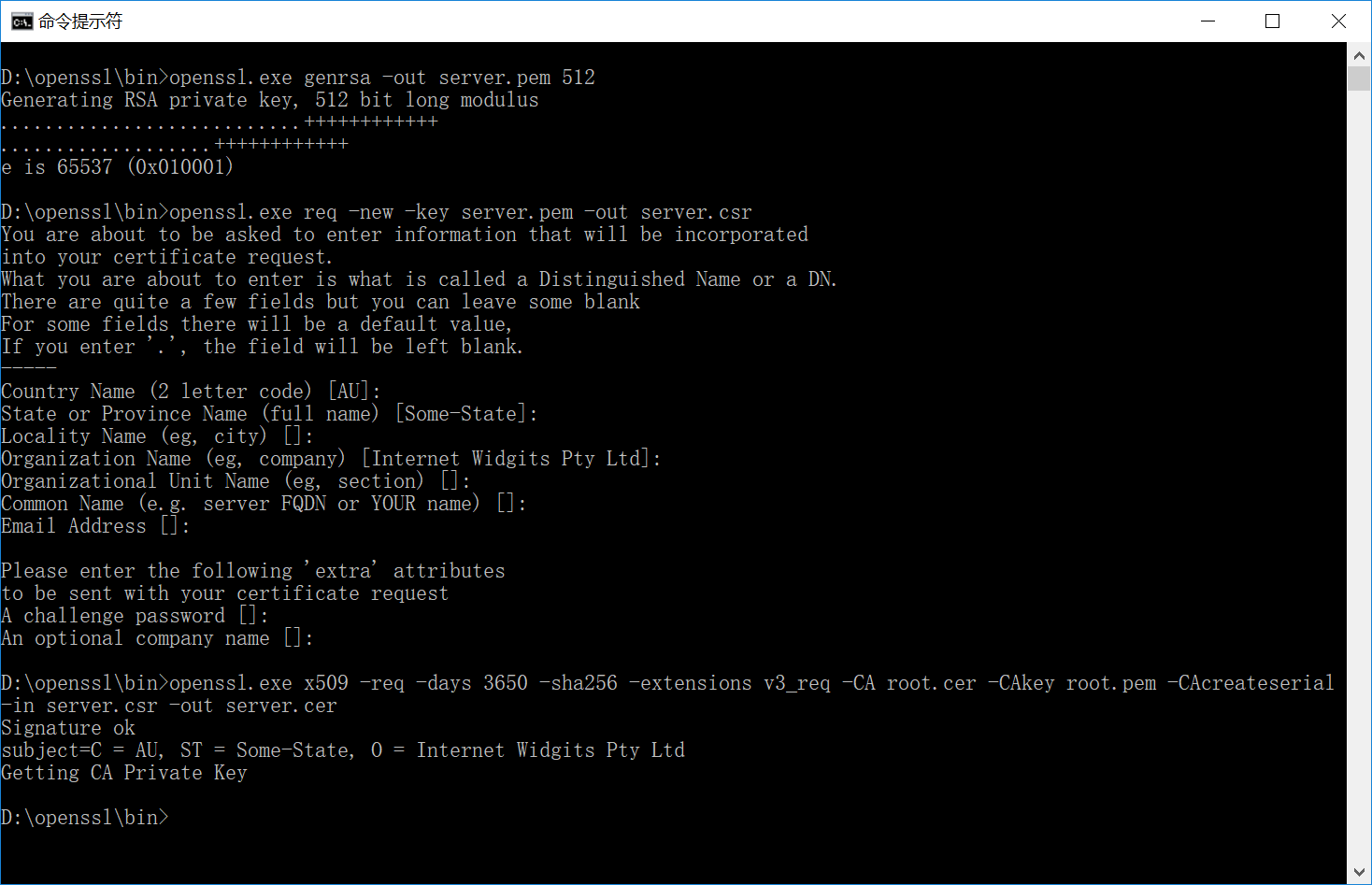
openssl生成服务器证书
用openssl生成服务器证书可以分为两步:
具体命令如下:
生成根证书秘钥 openssl.exe genrsa -out root.pem 512 创建根证书签发请求(csr:Certificate Signing Request)文件 openssl.exe req -new -key root.pem -out root.csr 创建一个有效期为10年的根证书 openssl.exe x509 -req -days 3650 -sha256 -extensions v3_ca -signkey root.pem -in root.csr -out root.cer 生成一个服务器证书秘钥 openssl.exe genrsa -out server.pem 512 创建服务器证书签发请求文件 openssl.exe req -new -key server.pem -out server.csr 用根证书签发服务器证书 openssl.exe x509 -req -days 3650 -sha256 -extensions v3_req -CA root.cer -CAkey root.pem -CAcreateserial -in server.csr -out server.cer